How to Protect Your Devices from Malicious Downloads: The internet is full of opportunities apps, games, tools, and free resources are just a click away. But along with the convenience comes a growing risk: malicious downloads.
Cybercriminals disguise malware as legitimate files, tricking users into installing programs that steal data, corrupt systems, or lock devices for ransom.
Why Malicious Downloads Are Dangerous
Malicious downloads can harm your devices in multiple ways:
- Data theft – Hackers steal personal details, banking information, or login credentials.
- Ransomware – Files are encrypted, and you must pay to unlock them.
- Spyware – Malware silently tracks your activities and keystrokes.
- System corruption – Devices slow down, crash, or become unusable.
- Botnets – Infected devices are controlled remotely to spread malware further.
Recognizing the risks is step one in staying ahead of these threats.
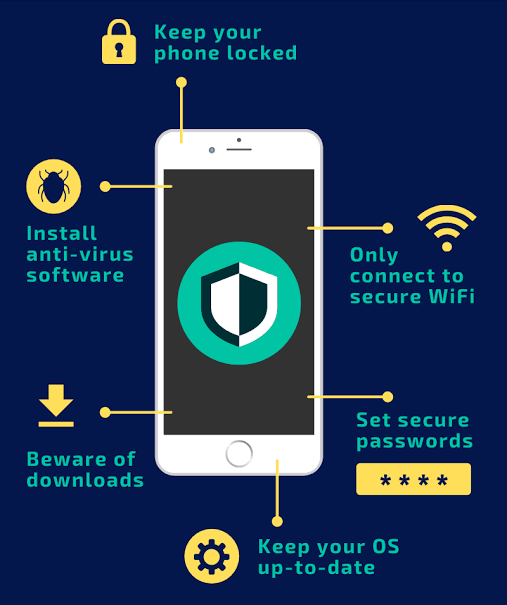
Step 1: Download Only from Trusted Sources
The safest way to protect yourself is to control where you get your software and files:
- Official websites: Always download apps directly from the developer’s official site.
- Reputable app stores: Use Google Play, Apple App Store, or Microsoft Store.
- Verified repositories: For open-source tools, stick to GitHub or SourceForge.
- Avoid shady sites: Be cautious of websites filled with ads, fake download buttons, or pirated content.
Pro Tip: Bookmark the official websites of software you use frequently to avoid falling for imitation sites.
Step 2: Use Antivirus and Antimalware Protection
Even the most cautious users can make mistakes. That’s where antivirus software comes in:
- Real-time protection – Stops malware before it installs.
- Regular scans – Detects hidden threats.
- Web protection – Warns you of malicious sites before you download.
Popular free antivirus options include Avast, Bitdefender, and AVG, while premium versions add extras like VPNs and firewalls.
Step 3: Enable a Firewall
Your firewall acts as a digital gatekeeper, monitoring what goes in and out of your device. Most operating systems come with built-in firewalls:
- Windows Firewall (enabled by default)
- macOS Firewall (can be activated in System Preferences)
- Mobile firewalls available through security apps
Make sure your firewall is turned on, and configure it to block suspicious activity.
Step 4: Check File Authenticity Before Downloading
A quick inspection can save you hours of headache:
- Verify the source: Does the file link come from the official website?
- Look at file extensions: Be wary of
.exe,.scr, or.batfiles when you’re not expecting them. - Use checksums: Developers often provide hash values (MD5/SHA). Verifying these ensures your file hasn’t been tampered with.
- Check file size: If the size doesn’t match what’s listed on the site, it may be infected.
Step 5: Scan Downloads Before Opening
Before you double-click, scan the file:
- Antivirus scan: Right-click the file and choose “Scan with…”
- Online tools: Services like VirusTotal let you upload and scan files against multiple antivirus engines.
- Sandboxing: Advanced users can run files in a virtual environment (sandbox) to test them safely.
Step 6: Keep Your System and Apps Updated
Cybercriminals exploit outdated software. Updates aren’t just about new features—they often include security patches that close vulnerabilities.
- Enable auto-updates for your operating system.
- Update apps regularly through official stores or directly from developers.
- Uninstall old software you no longer use, since abandoned apps won’t receive updates.
Step 7: Watch Out for Phishing Traps
Many malicious downloads start with a phishing attempt:
- Email attachments: Files disguised as invoices, resumes, or documents.
- Fake links: Buttons or URLs that lead to malicious sites.
- Social media scams: Downloads promoted through fake giveaways or contests.
Always verify the sender, hover over links before clicking, and avoid downloading attachments you weren’t expecting.
Step 8: Manage App Permissions on Mobile
Mobile devices are just as vulnerable:
- Check permissions: A flashlight app doesn’t need access to your contacts or microphone.
- Use trusted app stores only: Sideloading apps (installing outside official stores) is riskier.
- Regularly review apps: Uninstall those you don’t use or that ask for suspicious permissions.
Step 9: Backup Your Data Regularly
Even with precautions, there’s no 100% guarantee of safety. Backups ensure you can recover files if something goes wrong.
- Cloud backups: Google Drive, iCloud, OneDrive, or Dropbox.
- External drives: Keep a physical backup offline.
- Automated backups: Schedule regular syncs so you don’t have to remember manually.
If ransomware strikes, having backups can save you from paying hackers.
Step 10: Educate Yourself and Stay Vigilant
Cybersecurity isn’t just about tools—it’s also about awareness:
- Learn common red flags of malicious downloads.
- Stay updated on current threats via trusted cybersecurity blogs.
- Teach family members and coworkers safe practices.
The more informed you are, the less likely you’ll be caught off guard.
Common Red Flags of Malicious Downloads
- Pop-ups urging you to download “urgent” updates.
- Files that end in strange extensions like
.exe.pdf. - Too many “Download Now” buttons on one page.
- Offers that sound too good to be true (e.g., free premium software).
- Software that asks for your personal details before downloading.
READ ALSO: 5 Cybersecurity Software Every PC Needs in 2025
Real-World Example
Imagine you’re looking for a free PDF editor. A search shows dozens of sites, but some are filled with banners and flashy “Free Download” buttons. Instead of clicking the first link:
- You go to the developer’s official site (e.g., PDFsam Basic).
- You verify the file size matches what’s listed.
- You scan the installer with VirusTotal before running it.
- You perform a custom install to ensure no add-ons are included.
This extra 5 minutes of care saves you from installing hidden malware disguised as a free tool.
FAQs
What’s the biggest risk from malicious downloads?
Data theft and ransomware are the most common risks. Infected files can steal personal info or lock your device until you pay.
Is free software always risky?
Not at all. Many free tools are safe (like VLC or LibreOffice). The danger comes from downloading from unverified or shady sources.
How can I tell if a file is infected?
Scan it with antivirus software or upload it to VirusTotal. Also, watch for suspicious extensions like .exe when you were expecting a document or image.
Should I avoid downloading files altogether?
No. Downloading is safe if you follow precautions—use trusted sites, scan files, and avoid suspicious links.
Can mobile devices get infected too?
Yes. Malicious apps can steal contacts, track activity, or even lock your phone. Always use official app stores.
What if I accidentally download malware?
Disconnect from the internet, run a full antivirus scan, and remove the file. If necessary, boot into Safe Mode or use a professional malware removal tool.
Are browser downloads safe?
Yes, if you use trusted sites. Modern browsers like Chrome and Edge also warn you of unsafe files, but don’t rely on this alone.
Is pirated software dangerous?
Yes. Pirated files are a major source of malware. Even if the program works, it may secretly steal your data or install spyware.
How often should I back up my files?
Ideally, once a week or more frequently if you handle important data daily.
Do I need paid antivirus to stay safe?
Free antivirus offers basic protection, but premium versions provide advanced features like ransomware protection, firewalls, and phishing defense.